These types of email attacks rely on simple language and exploit human nature to scam their victims, making detection difficult, says Cisco Talos.

Image: GrafVishenka, Getty Images/iStockPhotos
The Business Email Compromise (BEC) attack is a popular tactic among cybercriminals. This type of scam requires less time and effort to implement than other kinds of cyberattacks. And the payoffs can be plentiful because these fraudulent emails are typically aimed at people and departments with the power to approve major purchases. A report released Tuesday by threat intelligence provider Cisco Talos examines the latest BEC scams making the rounds and offers advice on how to detect and prevent them.
SEE: Cybersecurity: Let's get tactical (free PDF)
BEC attacks can take different forms, but the basic premise remains the same. Though an email, the attacker impersonates a trusted contact, whether an internal executive or an external client.
The emails are often sent to people in an organization who have control over budgets or expenses. As with many phishing emails, the message focuses on an urgent request that requires the recipient's immediate response.
But with BEC campaigns, the goal is usually to steal money by claiming an overdue invoice, an outstanding bill, or even a need for gift cards or other types of payment.
In fact, the gift card ploy is one of the most common BEC tactics recently seen by Cisco Talos. In this type of scam, the attacker spoofs an executive or other trusted source claiming they need help buying a gift card for a family member. iTunes and Google Play gift cards are always popular items, but scammers have been hunting for PlayStation cards as well.
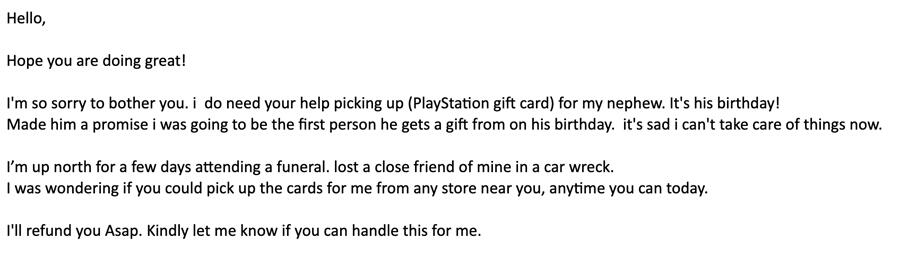
Image: Cisco Talos
BEC campaigns also continue to take advantage of the coronavirus pandemic. In this case, the scammer claims a need for gift cards but can't purchase them because they're supposedly infected with COVID-19.
These types of attacks can be challenging to thwart for a few reasons. The emails increasingly use common and straightforward language and take advantage of human nature to scam their victims. Preventing BEC messages from reaching your users can also be difficult as you want to stop them without blocking legitimate emails. Further, the message rarely include a malicious link or file attachment, which would otherwise cause a red flag for security software.
One trick offered by Cisco Talos is to identify suspicious emails that come from outside your organization. Here, the challenge is to figure out the right level of sensitivity. Too little, and these emails may still get through. Too much, and you risk blocking legitimate messages.
First, look into a security tool that offers advanced phishing protection, which includes sender authentication and additional BEC detection capabilities. Second, consider adding a tag to the subject line of external email. Such a tag can alert your users that the request came from an external source, prompting them to perhaps question or scrutinize the email more closely than they otherwise would. Third, make sure you educate your users on how to spot a BEC message and what to do if they receive one.
There are some questions you and your users should also ask when you receive a suspicious email. Why would an executive email you from a Gmail, Yahoo or Outlook address? Is this behavior typical? Would you usually respond to such a request? Is the sender using a generic email address?
Next, look for a reply-to address. Such an address is often found in marketing emails but shouldn't appear in personal or professional emails. When you try to reply to the message, does the reply address change, especially to one with an unfamiliar domain?
Finally, try to confirm the legitimacy of the source before you respond to the email. Contact the sender or sending company through an official email address, phone number or social media account. By verifying the actual sender and the message, you can more easily avoid being scammed before it's too late.

Cybersecurity Insider Newsletter
Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. Delivered Tuesdays and Thursdays
Sign up todayAlso see
- How to become a cybersecurity pro: A cheat sheet (TechRepublic)
- Kubernetes security guide (free PDF) (TechRepublic download)
- Information security policy (TechRepublic Premium)
- Online security 101: Tips for protecting your privacy from hackers and spies (ZDNet)
- All the VPN terms you need to know (CNET)
- Cybersecurity and cyberwar: More must-read coverage (TechRepublic on Flipboard)







 English (US) ·
English (US) ·